Introduction to Blockchains
Blockchains have become very popular in the last couple of years, and interest in them is increasing. If you search for stats on blockchain users over time, you will see something that looks like a straight line going up.
The speed of blockchain adoption is comparable to the internet adoption in the 90s and early 2000s. And if you overlay the number of blockchain users and the number of internet users, you'll find that we were now in 1998. This comparison shows that we are still very early in blockchain adoption. In 1998, Amazon was just an online book store, google was founded that year, and the concept of social media hadn't been invented yet.
Table of Content
Introduction
There are digital ledgers of transactions that duplicate themselves and distribute across networks of computers across the world. Some call it a Distributed Ledger Technology, or DTL for short. Each computer stores a record of all transactions on that network.
Decentralized Ledgers are not a new invention, though; the application and use-cases have grown with the rise of the internet. The use of Decentralized ledgers stretches back many thousands of years. The first recorded case was from 500 AD, around 1500 years ago. The people of Yap from Micronesia, located just north of Australia, came up with an alternative solution for their Fei stone problem – rather than recording their ledger centrally, they distributed the knowledge of Fei stone ownership across all the people of their village.
The Yapese highly valued the Fei stones and used them as significant ceremonial gifts. The ownership of a large stone was established by its history. It would be too difficult to move, so its ownership was recorded in oral tradition rather than by its location.
Every villager kept a mental record of who owned each stone, where they got it from, and when that transaction took place.
When a villager spent a Fei stone, this was recorded as a new transaction, and that new transaction was shared across the village people to update everyone's mental map – just like a very ancient, early take on DTL.
If someone came along and tried to claim a stone was theirs wrongly, the village could consult its Decentralized mental ledger.
A blockchain is essentially a digital ledger of transactions duplicated and distributed across the entire network of computer systems on the blockchain. Each block in the chain contains several transactions, and every time a new transaction occurs on the blockchain, a record of that transaction is added to every participant's ledger.
What is a Blockchain?
A blockchain is a series of blocks chained with inseparable links called hashes.
Four key concepts must be understood: 1) blocks, 2) transactions, 3) hashes, and 4) chains.
The relation between the concepts is that each block contains transactions. A hash links the blocks together. A chain is a sequence of blocks.
A blockchain must beat like a metronome that produces blocks at set intervals. Those intervals can be random or can have a predefined schedule. The critical part is that the beating can not stop, and a blockchain must always produce blocks. A blockchain that creates blocks at regular intervals, uninterrupted, is functioning well. If a blockchain stops for any reason, this is a problem and is usually a sign that something has gone wrong.
Like a metronome beating, a blockchain produces blocks at regular intervals.
What are transactions?
Transactions are records of what happens on the blockchain and include all sorts of information. To the extent that a blockchain is a giant decentralized ledger, transactions are actions that change the values in this decentralized ledger.
Examples of transactions:
- Updating any value stored on the blockchain
- Sending bitcoins to someone else
- Interacting with a smart contract
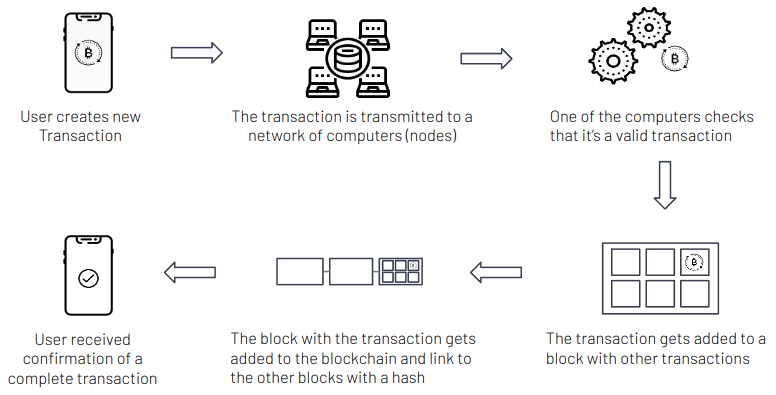
A transaction originates from a user on his computer or a mobile phone. The user sends the transaction to one of the special computers connected to the blockchain (called a Node). The computer then tells all the other computers that one of them needs to add the transaction to the next block. The consensus algorithm decides which computers get to add the transaction to the next block (more on this in a separate section below). The user gets a confirmation when a computer adds their transaction to a block.
Transactions on the Blockchain take time to process. They need to be communicated to all the Nodes on the network and then need to get added to the next block. Blockchains have different settings for how often blocks get created.
Average blocks times across three major blockchains:
- Bitcoin blockchain: 10 minutes;
- Ethereum blockchain: 14 seconds.
- Cardano blockchain: 20 seconds.
Therefore if we take Cardano as an example, a transaction can take up to 20 seconds to be processed. It is also possible that a transaction does not get added to the next block and might need to wait for a little longer.
What is a block?
A block is a group of transactions that gets added to the end of a blockchain. A block can be empty, contain no transaction, and still be added to the end of a blockchain. The blockchain produces blocks at regular intervals, like a beating metronome, and it will always create blocks.
When a new blockchain is created, and there aren't many people using it, a large proportion of the blocks are often empty. It is also possible that during quiet time, blocks can be empty.
Each block needs to contain at least the following information
- A hash of all the transactions in that block
- A hash of the previous block
- The transactions included in that blocks
Each block needs to contain the previous block's hash so that it is clear where it sits in the order of the other blocks. This iterative process confirms the integrity of the last block, all the way back to the initial block
A block often includes additional information, but it is not strictly required for a functional blockchain. Some of the other information that the block usually includes:
- The Node (computer) that added the transactions to the blockchain
- Block number
- Timestamp
What is a hash?
A hash is a cryptographic concept that can turn an arbitrary amount of data into a fixed string. This string is called the hash value. And changing just a tiny amount of the data would result in a completely different hash value. The hash also has a convenient property that no one can reverse.
The function that takes an arbitrary amount of data and turns it into a hash value is called a hash function. And there are many different hash functions. For example, the hash function that Bitcoin uses is called the SHA-256 and is part of a family of hashing algorithms called SHA-2.
Example of SHA-256:
Data: "Nature is Beautiful"
Hash: 228279b0f26ecd1e23da4ab4a...9fddd2977b66b8574
Data: "Nature is beautiful" with a small b
Hash: c4d43767a536775581b3faf19...2fd45d9add367dc72a
Changing the first letter of Beautiful to beautiful completely changes the hash value. And someone who sees only the hash value will never find out what the actual phrase is
Hash functions are also widely used in the government and private sectors, and the law requires their use for some specific US Government applications.
How are hash functions relevant to the blockchain?
Each block on the blockchain contains its unique hash and the block's unique hash before it. If someone edits the information on a block, that block's hash code changes—however, the hash code on the block after it would not. This discrepancy makes it extremely difficult for information on the blockchain to be changed without notice.
The hash functions, therefore, make the blockchain secure. Once a block is created, the data inside that block generates a particular hash value. This hash value then gets recorded in the following blocks and so forth in the blocks after that.
If someone changes the data in any block, its hash value will change, making the rest of the blockchain incompatible.
What is a chain?
The chain is the sequence of blocks connected with the hash values. The data inside each block determines the block's hash values, and each block also contains the hash value from the previous block, thus creating a sequence.
There can be times when a chain splits in two; this happens when more than one block is created simultaneously. This happens because there are multiple Nodes in a blockchain, and each Node competes to be next to add a block to the blockchain. And sometimes, two Nodes create a block at the same time.
When more than one block is created, this temporarily makes 2 forks of a blockchain, and then when the next block gets added, the Node will look at the two forks and pick one with a higher "credibility" score. The whole network will continue adding blocks to the most credible fork. The other fork will get discarded. The transactions from the discarded block will be rerouted and included in one of the following blocks.
The occurrence described above happens regularly on any blockchain without the users noticing anything. Another type of a form is called a "Hard Fork" where the chain split intentionally and an upgrade to the software is required. More on this further in the article
Who Manages the Blockchain?
Blockchain networks rely on a decentralized infrastructure that any person or group can't control. Unlike political regulation, blockchain governance is not emergent from the community. Instead, it is ex-ante, encoded in the protocols and processes as an integral part of the original network architecture. To be a part of a community supporting a blockchain is to accept the rules of the network as they were initially established
Blockchain technology can algorithmically enforce private agreements and community principles at a global scale by shifting the cost of trust and coordination to the network. This trustless nature of blockchains allows them to create new markets where they couldn't exist before, whether for political or economic reasons. To do this, we must be able to trust the blockchain and that no one controls it.
A Trustless Technology
Blockchains enable transactions between individuals with certain technological guarantees. The network relies on cryptography to verify that transactions are correct. Unlike a traditional system with a centralized operator such as a bank, all transactions occur via a protocol. There is a degree of transparency: no one can violate the use of the protocol because the network will reject the transaction. Also, information recorded on blockchain can never be removed or modified. Those features combined create what we call a "trustless" system.
In a blockchain transaction, you don't have to trust your counterpart to perform their obligations or correctly record transactional data since these processes are standardized and automated. Still, you must rely on the code and the network to function as you expect.
The different layers of a Blockchain
Due to the lack of a centralized authority, blockchains must be very safe. They must also be highly scalable to handle increasing users, transactions, and other data. Layers were born out of the requirement for scalability concurrent with security preservation.
There are five layers in blockchain architecture.
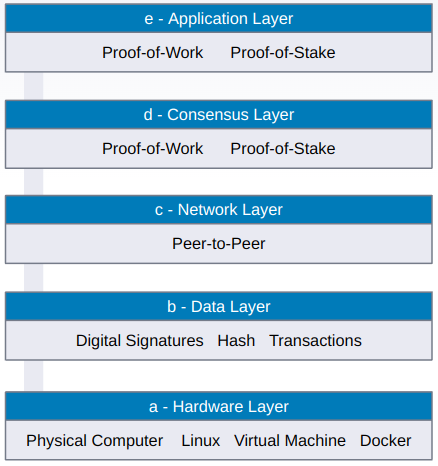
a) Hardware infrastructure layer
Servers in data centers or individual homes store the blockchain's content. Clients request content or data from application servers while browsing the web or utilizing any apps, known as the client-server architecture.
Clients can now connect with peer clients and share data. A peer-to-peer (P2P) network is a large group of computers that share data. Blockchain is a peer-to-peer network of computers that computes, validates, and records transactions in an orderly manner in a shared ledger. As a result, a distributed database is created, storing all data, transactions, and other pertinent data. A node is a computer in a P2P network.
b) Data layer
A blockchain's data is the sequence of blocks connected with the hash values. The data inside each block determines the block's hash values, and each block also contains the hash value from the previous block, thus creating a sequence.
To protect the security and integrity of the data contained in the blockchain, transactions are digitally signed. A private key is used to sign transactions, and anyone with the public key may verify the signer. In addition, the digital signature detects information manipulation. Because the encrypted data is also signed, digital signatures ensure unity. As a result, any manipulation will render the signature invalid.
c) Network layer
The network layer, called the P2P layer, is responsible for inter-node communication. In addition, the network layer handles discovery, transactions, and block propagation.
This P2P layer ensures that nodes can find one other and interact, disseminate and synchronize to keep the blockchain network in a legitimate state. A P2P network is a computer network in which nodes are distributed and share the workload of the network to achieve a common purpose. Nodes carry out the blockchain's transactions.
d) Consensus layer
The consensus layer is in charge of validating the blocks, ordering them, and guaranteeing that everyone agrees. Each blockchain has its implementation of the consensus layer. And this is the area most research goes into
Essential elements of a consensus layer:
- The consensus layer establishes a clear set of agreements among nodes in a distributed P2P network
- The consensus layer ensures that power stays decentralized and diffused. As a result, no single party has complete control over the blockchain.
- The consensus layer ensures that only one chain is followed and that it contains the truth.
- The consensus layer consists of the rules to which nodes adhere so that transactions are validated, and blocks are established in a manner consistent with those rules.
- The consensus layer achieves unanimity of truth acceptance among the participating nodes
- In a P2P network, the consensus protocol aids in achieving reliability
e) Application layer
Smart contracts and Decentralized Applications (DApps) make up the application layer. The application layer protocols are further subdivided into the application and the execution layers. The application layer comprises end-user's programs to communicate with the blockchain network. Scripts, application programming interfaces (APIs), user interfaces, and frameworks are part of it.
Blockchain Trilemma
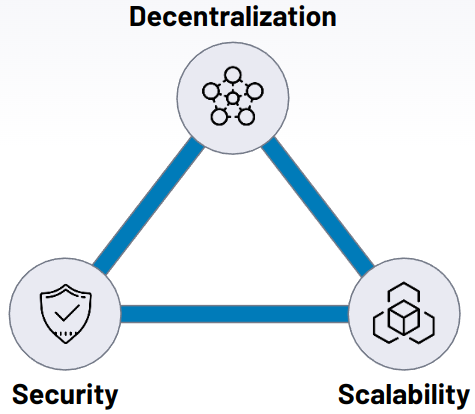
The blockchain trilemma refers to the commonly held notion that decentralized networks can only provide two out of the three benefits at any given time in terms of decentralization, security, and scalability.
Computer scientists devised the consistency, availability and partition tolerance (CAP) theorem in the 1980s to express possibly the most significant of these difficulties. The CAP theorem states that decentralized data storage, such as blockchain, can only satisfy two of the three guarantees mentioned above simultaneously.
This theorem has evolved into the blockchain trilemma in the context of the current distributed networks. The fundamental notion is that public blockchain infrastructure must sacrifice security, decentralization, or scalability.
As a result, the difficult problem that must be addressed when designing a network is how to create a network with impenetrable security over a broadly decentralized network while also handling internet-scale transactional throughput. A blockchain cannot optimize for all three desired features simultaneously, forcing it to make trade-offs.
In general terms:
- The blockchain's scalability refers to its ability to handle a higher volume of transactions.
- Security refers to securing data on the blockchain from various types of assaults and the blockchain's defense against double-spending.
- Decentralization is a type of network redundancy that ensures that fewer entities do not control the network
A pragmatic solution to address the trilemma seems to be splitting the blockchain into Layer 1 and 2. So Layer 1 is responsible for being very decentralized and secure but not overly fast. So a, Layer 2 is added on top that borrows the decentralization and security from Layer 1 and adds scalability - so that the blockchain becomes fast and cheap
Layer 1 and Layer 2
Layers 1 and 2 are different from the layer described in the previous section and are generally discussed in the context of the scaling problem and solutions.
Layer 1 refers to the base level of blockchain architecture. It's the main structure of a blockchain network. Bitcoin, Ethereum, and Cardano are examples of Layer 1 blockchains. Layer 2 refers to networks built on top of other blockchains. So if Bitcoin is a Layer 1, the Lightning Network that runs on top of it is an example of a Layer 2.
The networks on top of Layer 1 (the base layer) are known as Layer 2 solutions. Protocols use layer two to increase scalability by removing some interactions from the base layer. As a result, smart contracts on the primary blockchain protocol only deal with deposits and withdrawals and ensure that off-chain transactions follow the regulations.
The blockchain is the first layer in a decentralized ecosystem. Layer 2 is a third-party integration used in conjunction with layer one to enhance the number of nodes and, as a result, system throughput.
There are several alternative approaches how to implementing Layer 2's
a) Rollups - These bundle off-chain Layer 2 transactions and submit them as one transaction on the main chain. These systems use validity proofs to check the integrity of transactions. Assets are held on the original chain with a bridging smart contract, and the smart contract confirms the rollup is functioning as intended. This provides the security of the original network with the benefits of a less resource-intensive rollup.
b) Sidechains - A sidechain is a transactional chain that runs alongside the blockchain and is used for massive bulk transactions. Sidechains have their consensus method, which can be adjusted for speed and scalability. A utility token is frequently utilized as a part of the data transfer mechanism between side and main chains. The main chain's principal function is to provide general security and dispute resolution.
c) State channels - A state channel improves total transaction capacity and speed by facilitating two-way communication between a blockchain and off-chain transactional channels via various approaches. To validate a transaction over a state channel, the miner does not need to be involved immediately.
Instead, it's a network-adjacent resource protected via a multi-signature or smart contract mechanism. The ultimate "state" of the "channel" and all its inherent transitions are posted to the underlying blockchain when a transaction or batch of transactions is completed on a state channel.
State channels examples include Bitcoin Lightning and Cardano's Hydra. In the trilemma trade-off, state channels give up some decentralization in exchange for increased scalability.
Forks
There are frequent forks throughout the day but users don't notice as the chain automatically picks the dominant form. However, there are also other types of forks that result from software upgrades to Nodes that affect how a blockchain operates and need Node operators' involvement.
There are Soft Forks and Hard Forks
A soft fork changes the software protocol where only previously valid transaction blocks are made invalid. Because old nodes will recognize the new blocks as valid, a soft fork is backward-compatible.In addition, this kind of fork requires only a majority of the miners to upgrade to enforce the new rules, as opposed to a hard fork that requires all nodes to upgrade and agree on the latest version.
The more miners accept the new rules, the more secure the network post-fork. If you have 3/4 of miners recognizing the fork, 1/4 blocks created aren't guaranteed to follow the new rules. These 1/4 blocks will be valid to old nodes that aren't aware of the new rules, but new nodes will ignore them.
A hard fork is a radical change to a network's protocol that makes previously invalid blocks and transactions valid, or vice-versa. A hard fork requires all nodes or users to upgrade to the latest version of the protocol software.
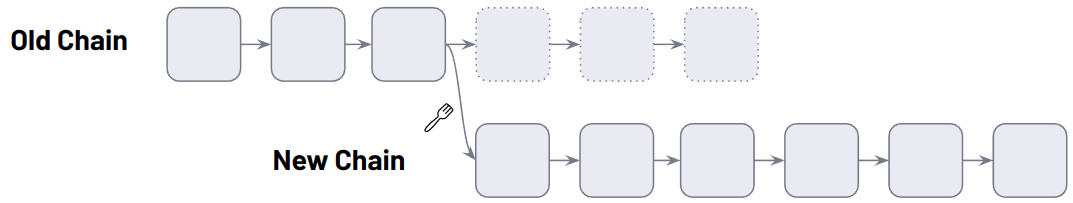
In both soft and hard forks, the old chain is replaced by a new chain.
Public Blockchains
A public blockchain network is a blockchain network where anyone can join whenever they want. There are no restrictions when it comes to participation. More so, anyone can see the ledger and take part in the consensus process.
Bitcoin is a public blockchain that laid the foundation of blockchain technologies. Ethereum and Cardano are also public blockchains, and there are many others.
Private blockchains are special types of blockchain technology where only a single organization has authority over the network. The private blockchain solutions have an authorization scheme to identify who is entering the platform. Private blockchain solutions develop these platforms for the internal networking system of a company. A private blockchain is not decentralized like public blockchain platforms. We will not cover these as there are too many possible variations and are specific to individual organizations, for a discussion on its merits you can consult this resource.
Bitcoin
Bitcoin is a digital form of cash. But unlike the fiat currencies you're used to, there is no central bank controlling it. Instead, thousands of computers distributed around the world run Bitcoin. Anyone can participate in the ecosystem by downloading open-source software.
Bitcoin was the first cryptocurrency, announced in 2008 (and launched in 2009). It provides users with the ability to send and receive digital money. Many appreciate its permissionless nature – anyone with an Internet connection can send and accept it. It is cash that no one can stop you from using, but its digital presence means that anyone can transfer it globally. In addition, Bitcoin is decentralized, censorship-resistant, secure, and borderless.
Nobody knows who created Bitcoin! Its creator used the pseudonym Satoshi Nakamoto, but we don't know anything about their identity. Satoshi could be one person or a group of developers anywhere in the world. More on this in the next chapter.
Bitcoin has a finite supply, but not all units are in circulation yet. So the only way to create new coins is through mining – the particular mechanism for adding data to the blockchain.
The protocol fixes Bitcoin's max supply at twenty-one million coins. As of 2020, just under 90% of these have been generated, but it will take over one hundred years to produce the remaining ones. This is due to periodic events known as halvings, which gradually reduce the mining reward.
Who is Satoshi Nakomoto?
Satoshi Nakamoto is the pseudonym behind the development of Bitcoin and the authorship of the original Bitcoin whitepaper. The question "who is Satoshi Nakamoto?" has led to speculation of their true identity and people falsely claiming they are Satoshi Nakamoto.
Satoshi didn't invent blockchain, but he was the first to create a decentralized currency based on blockchain technology.
Before Satoshi cut off all communications in April 2011, they claimed to be male, Japanese and born on April 5, 1975. However, people have observed that Satoshi's command of English was so high that they're likely to be from a native-English speaking country. Also, their communications mainly occurred during European working hours, so it's speculated they didn't reside in Japan.
With Satoshi Nakamoto no longer on speaking terms with the rest of the world, speculation has run wild regarding their true identity. Plenty of people and groups have been labeled as the true Satoshi Nakamoto, but only a handful of candidates have proven notable.
Hal Finey - Hal was an early user of Bitcoin and the recipient of the first Bitcoin transaction. He also worked as a software developer and was one of the original cypherpunks in the 1990s. Sadly, Hal Finney passed away in 2014 after suffering from a nerve disease that left him paralyzed for some time before his death. He always denied that he was Satoshi Nakamoto.
Nick Szabo - Nick is a computer scientist who created a "bit gold" digital currency years before Bitcoin. His communications within the cypherpunk community overlapped strongly with Satoshi's, as did his writing mannerisms and communication times.
Nick has denied that he is Satoshi Nakamoto. However, there are many parallels between Nick and Satoshi.
Dorian Nakamoto - Dorian is a Japanese-American man whose birth name is Satoshi Nakamoto. He's worked as a computer engineer for technology and financial services companies and even lived in the same area in California as Hal Finney for over a decade
There are many claims as to who Satoshi Nakamoto truly is. They could be a single person or a group of people. They could be dead or alive. But without solid, concrete evidence, we'll never truly know who Satoshi Nakamoto is
Largest Public Blockchains
There are many more blockchains other than Bitcoin. Below we will cover just the main ones by market size
Ethereum (ETH) - Ethereum (ETH) was the first smart contract platform. It is a decentralized software platform that enables smart contracts and decentralized applications (dApps) to be built and run without any downtime, fraud, control, or interference from a third party. The goal behind Ethereum is to create a decentralized suite of financial products that anyone in the world can freely access, regardless of nationality, ethnicity, or faith.4 This aspect makes the implications for those in some countries more compelling because those without state infrastructure and state identifications can get access to bank accounts, loans, insurance, or a variety of other financial products.
Ethereum runs on a Proof-of-Work algorithm similar to Bitcoin and is planning to transition to a Proof-of-Stake consensus algorithm in 2022/23
Solana (SOL) - Founded in 2017, Solana is a blockchain platform that supports decentralized applications (dApps). Solana performs many more transactions per second than Ethereum. Additionally, it charges lower transaction fees than Ethereum at a compromise of being less reliable.
Both Solana and Ethereum can create smart contracts, which are essential for running cutting-edge applications, including decentralized finance (DeFi) and non-fungible tokens (NFTs). Solana runs on a Proof-of-Stake consensus algorithm.
Cardano (ADA) - Cardano is a Proof-of-Stake blockchain created with a research-based approach by engineers, mathematicians, and cryptography experts. The project was co-founded by Charles Hoskinson, one of the five initial founding members of Ethereum.
The team behind Cardano created its blockchain through extensive experimentation and peer-reviewed research. The researchers behind the project have written more than 120 papers on blockchain technology across various topics. This research is the backbone of Cardano.
Polkadot (DOT) - Its protocol is designed to connect private and permissionless blockchains and oracles to allow systems to work together under one roof. Polkadot's core component is its relay chain, which enables the interoperability of varying networks. It also provides parachains, or parallel blockchains with their native tokens for specific-use cases.
Polkadot differs from Ethereum in that rather than creating dApps on Polkadot; developers can create their blockchain while also using the security that Polkadot's chain already has. With Ethereum, developers can create new blockchains but need to make their security measures, which can leave new and smaller projects open to attack. The more significant a blockchain, the more security it has. This concept in Polkadot is known as shared security.
Gavin Wood created Polkadot, he was another member of the core founders of Ethereum.
Binance Chain (BNB) - Binance Chain uses a modified version of the Proof-of-Stake consensus, called Proof of Staked Authority (PoSA). It is also a platform on which Binance's decentralized exchange operates. Changpeng Zhao founded the Binance Exchange, one of the world's most widely used exchanges based on trading volumes.
Polygon (MATIC) - Polygon is a layer two scaling solution aiming to further scale the Ethereum blockchain network. It is built on the Ethereum blockchain, enabling fast transactions with low fees. It was launched in 2017 and has emerged as one of the top layer two scaling solutions that improve the scalability of the Ethereum blockchain network. The platform uses the Ethereum blockchain to connect Ethereum-based projects. The platform currently supports more than 7,000 blockchain-based projects.
Interoperability between Blockchains
Blockchain interoperability allows data and value to be transferred across different networks. In an interoperable system, once disparate blockchain networks and assets can easily plug into and be combined. This network interoperability may allow for creating powerful new products and services that simultaneously leverage the benefits of multiple blockchain networks.
The ability of blockchain protocols and applications to mix and match different "lego pieces" is key to creating entirely new Web3 instruments and platforms that aren't possible with legacy industries and business models of the Web2 era. Interoperable smart contracts could supercharge industries like healthcare, law, or real estate, for instance, by allowing important business information to be sent back and forth between private and public networks in a customizable and controllable manner. In addition, blockchain interoperability may enable multi-token transactions and wallet systems, which would significantly streamline the crypto user experience.
Decentralization within individual blockchain networks is a priority for many blockchain projects; the ability to establish network interoperability across multiple blockchains presents an even more advanced embodiment of blockchain technology's promise to decentralize systems and economies. Instead of having one blockchain like Ethereum processing all the transactions for thousands of decentralized applications (dApps), there could one day be thousands of application-specific blockchains that communicate with one another.
At present, interoperability is achieved using cross-chain bridges and swaps. Cross-chain bridges enable a digital asset owned by a party to be locked on one chain while an identical asset is "minted" on another chain and sent to an address owned by the original owner. In contrast, atomic swaps enable users to exchange tokens from different blockchain networks in a decentralized manner. Both are automatically enabled through smart contracts and play a central role in facilitating seamless cross-chain value transfers.
Consensus Algorithm
A consensus algorithm is a mechanism that allows users or machines to coordinate in a distributed setting. It must ensure that all agents in the system can agree on a single source of truth.
In a centralized setup, a single entity has power over the system. In most cases, they can make changes as they please – there isn't some complex governance system for reaching consensus amongst many administrators.
But in a decentralized setup, it's a whole other story. For example, say we're working with a distributed database – how do we reach an agreement on what entries get added?
Overcoming this challenge in an environment where strangers don't trust each other was perhaps the most crucial development paving the way for blockchains. In this article, we'll take a look at how consensus algorithms are vital to the functioning of cryptocurrencies and distributed ledgers.
Proof-of-Work
Proof of Work (PoW) is the godfather of blockchain consensus algorithms. It was first implemented in Bitcoin, but the actual concept has been around for some time. In Proof of Work, validators (referred to as miners) hash the data they want to add until they produce a specific solution.
A hash is a seemingly random string of letters and numbers that are created when you run data through a hash function. But, if you run the same data through it again, you'll always end up with the same output. Change even one detail, though, and your hash will be completely different.
Looking at the output, you can't possibly tell what information was fed into the function. They're therefore useful for proving that you knew a piece of data before a certain time. You can give someone its hash, and when you later reveal the data, that person can run it through the function to make sure the output is the same.
In Proof of Work, the protocol sets out conditions for what makes a block valid. It might say, for instance, that only a block whose hash begins with 00 will be valid. The only way for the miner to create one that matches that combination is to brute-force inputs. They can tweak a parameter in their data to produce a different outcome for every guess until they get the right hash.
With major blockchains, the bar is set incredibly high. To compete with other miners, you would need a warehouse full of special hashing hardware (ASICs) to be in with a chance of producing a valid block.
Your stake, when mining, is the cost of these machines and the electricity required to run them. ASICs are built for one purpose, so they have no use in applications outside of cryptocurrency mining. Your only way to recoup your initial investment is to mine, which yields a significant reward if you successfully add a new block to the blockchain.
It's trivial for the network to verify that you have indeed created the right block. Even if you've tried trillions of combinations to get the right hash, they just need to run your data through a function once. If your data produces a valid hash, it will be accepted, and you'll get a reward. Otherwise, the network will reject it, and you'll have wasted time and electricity for nothing.
Mechanisms for achieving consensus are vital to the functioning of distributed systems. Many believe that the greatest innovation in Bitcoin was the use of Proof of Work to enable users to agree on a shared set of facts.
Consensus algorithms today underpin not only digital money systems, but blockchains allowing developers to run code across a distributed network. They're now a cornerstone of blockchain technology and are critical to the long-term viability of the various networks in existence.
Proof-of-Stake
Proof of Stake (PoS) was proposed in the early days of Bitcoin as an alternative to Proof of Work. In a PoS system, there's no concept of miners, specialized hardware, or massive energy consumption. All you need is a regular PC.
Well, not all. You still need to put some skin in the game. In PoS, you don't put forward an external resource (like electricity or hardware), but an internal one – cryptocurrency. Rules differ with every protocol, but there's generally a minimum amount of funds you must hold to be eligible for staking.
From there, you lock up your funds in a wallet (they can't be moved while you're staking). You'll typically agree with other validators on what transactions will go into the next block. In a sense, you're betting on the block that will be selected, and the protocol will choose one.
If your block is selected, you'll receive a proportion of the transaction fees, depending on your stake. The more funds you have locked up, the more you stand to gain. But if you attempt to cheat by proposing invalid transactions, you'll lose a portion (or all) of your stake. Therefore, we have a similar mechanism to PoW – acting honestly is more profitable than acting dishonestly.
Once PoS is rolled out on a network with a large amount of value, the system becomes a playing field of game theory and financial incentives. Anyone with the know-how to "hack" a PoS system would likely only do so if they could gain from it – therefore, the only way to find out if it's feasible is on a live network.
Global Adoption & Gartner Projections
According to a study from April 2022 by Finder.com, roughly 10% of Americans owned cryptocurrencies and ~15% worldwide. The worldwide adoption is skewed by developing countries such as El Salvador and Nigeria. Global crypto ownership rates are heavily skewed toward the young,
Consider the adoption of the internet in 1990 when only a handful of governments, universities, businesses, and individuals were using the internet. But in the year 2000, everyone had to have a website. Similarly, smartphones were scarce in 2007 when the iPhone was invented, but by 2011 every person over the age of 12 was carrying around the internet in their pocket.
2021 was a big year for blockchains and cryptocurrency.
We've seen Bitcoin hit multiple new all-time high prices over the past year — followed by significant drops — and more institutional buy-in from major companies. Ethereum, the second-biggest cryptocurrency, notched its new all-time high late last year. U.S. government officials and the Biden administration have increasingly expressed interest in new regulations for cryptocurrency.
All the while, people's interest in crypto has skyrocketed: it's a hot topic not only among investors but in popular culture too, thanks to everyone from long-standing investors like Elon Musk
With each passing year, we are seeing new developments come out of the space and capture the minds and pocketbooks of people worldwide. For example, NFTs have taken the Philippines by storm, and the bitcoin lightning network is used by the people of El Salvador for day-to-day transactions.
CBDCs
Governments are building their digital currencies, called CBDCs (Central Bank Digital Currencies). Although they may be launched within the next decade, a certain amount of digital literacy is going to be required before they can be rolled out en-masse. Although cryptocurrencies and CBDCs are likely to work differently, many fundamentals may appear to be the same. For example, instead of pulling out physical bills from your wallet, payments will likely be made using a digital wallet on your smartphone. In addition, like cryptocurrencies, independent financial technologies will be built around the CBDC rather than within traditional financial institutions like banks.
Projections from Gartner
Gartner, Inc is technological research and consulting firm based in the US that researches technology. It gained notoriety through publications of the Magic Quadrant, which compares the relative competitive advantages of companies in the tech industry.
For the blockchain industry, Gartner developed a methodology called the Blockchain Spectrum. The Blockchain Spectrum is made up of four archetypes broken down by the characteristics and elements they contain
- Blockchain 1.0 - Enabling Technology (pre 2010). The technologies that formed the foundation; cryptography and peer-to-peer networks, for example. This phase ran until around 2012.
- Blockchain 2.0 - Blockchain Inspired (mid 2010s). The current phase, where pilots and proofs of concepts are being explored and sometimes deployed.
- Blockchain 3.0 - Blockchain Complete (2023+). The next phase where all five elements will be integrated into enterprise solutions.
- Blockchain 4.0 - Enhanced Blockchain (2025+). The internet of things (IoT) and self-sovereign identity (SSI) will converge with blockchain solutions. This will allow automation and transactions on a vast scale.
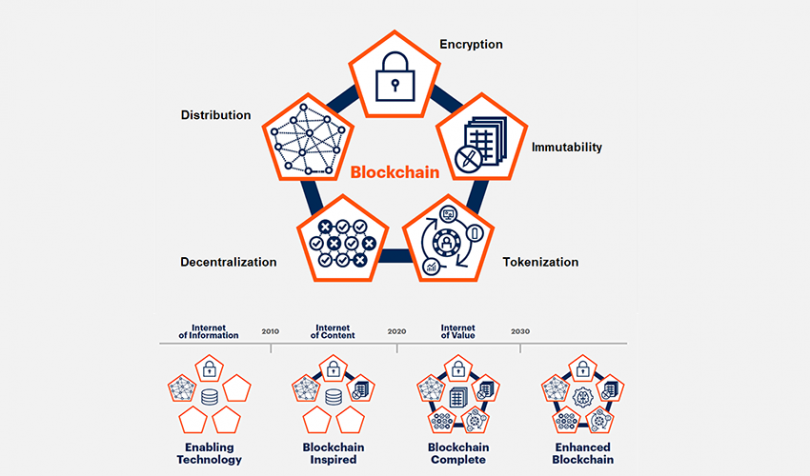
Blockchain-enabling
These technologies provide the foundation for organizations to create future blockchain solutions. These blocks can also be used as part of non-blockchain solutions, for example, to improve the operational efficiency of distributed data management systems. The building blocks include cryptography, distributed computing, peer-to-peer networking, and messaging
Blockchain-inspired
Technologies that focus on efficiency or reengineering existing processes. For example, Alibaba tracks and traces food products from around the world. Blockchain-inspired solutions will dominate enterprise implementation focus through the early 2020s. However, these solutions are generally of limited scope and rely on maintaining established processes and architecture such as a centralized notary, distributed or replicated data stores, hashing/signing, and a messaging layer. Critically, they cannot tokenize multiple forms of digital and non-digital assets and are designed without a basis for decentralized operations and governance.
Blockchain-complete
Beginning around 2023, enterprise-ready blockchain-complete solutions will emerge. These will offer a path to new business models that use dynamic smart contracts, tokenization, and decentralized operational structures. These solutions will deliver on the full value proposition of blockchain. Blockchain-complete solutions will feature tokenization enabled by smart contracts and decentralization (which current blockchain-inspired systems in the corporations' lack)
These capabilities are the catalysts for the introduction of new business models. The introduction and use of blockchain-enabled tokens will allow for previously impossible value exchange systems, notably at a micro-level. To distinguish these solutions from blockchain-inspired solutions, investigate how the technology is implemented; how the solution handles data; where the data controls sit; whether tokenization is an inherent design facet; how transaction governance is enabled; and how on-chain/off-chain data synchronization occurs.
Blockchain-enhanced
Moving into 2025, blockchain will incorporate complementary technologies, such as the Internet of Things (IoT), artificial intelligence (AI), and decentralized self-sovereign identity (SSI). This evolution will enable people to own, control, and share their digital and non-digital identities via decentralized SSI. Individuals can decide how their identities will be shared, leading to a situation when organizations, people, or things can use that data as needed for interaction. All the data will be secured, for example, in a digital wallet and be traceable and trackable. These solutions will also expand the types of value that can be tokenized and increase the number of microtransactions enabled by smart contracts.
For example, this could lead to a car negotiating its insurance rates directly with the insurance company based on data collected by the car's sensors. Blockchain-enhanced solutions will lead to business model changes as autonomous agents gain the ability to interact and operate independently of a human commercially. CIOs should begin exploring and evaluating current market solutions and discussing the potential for massive shifts to the rest of the business.
Slides
TBC
References
Text
- Blockchain on Wikipedia
- Blockchains on Investopedia
- Blockchain from 1000 years ago
- The Island of Yap and the idea of Money
- How does a hashing algorithm work
- Soft Forks and Hard Forks
- What is a Blockchain Consensus Algorithm
- Who is Satoshi Nakamoto
- What is Bitcoin
- Who Controls the Blockchain?
- The Gartner Blockchain Spectrum
- Layers of Blockchain Technology
- Layer 1 vs. Layer 2 Scaling Solutions
- Cross-chain Interoperability
- 10 Important Cryptocurrencies Other than Bitcoin
- Global Crypto Adoption Index 2021
- Crypto Mass Adoption: A Matter of When, Not If - Nasdaq
- Finder Cryptocurrency Adoption Index
- Adoption of Blockchain and Cryptocurrencies - Time
Videos
License
This work is distributed under a Creative Commons Attribution 4.0 International (CC BY 4.0) The license allows you to copy and redistribute the material in any medium or format, as well as remix, transform, and build upon the material for any purpose, including commercial, as long as you give appropriate credit to the creator.