Addresses and Keys
In cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random. Like a physical key, it locks (encrypts) data so that only someone with the right key can unlock (decrypt) it.
Table of Content
Introduction
Cardano uses asymmetric encryption for the majority of its encryption. Symmetric encryption, also known as public-key encryption, uses a public key-private key pairing: data encrypted with the private key can only be decrypted with the public key, and vice versa.
To make this concept clear, we can try a visual example.
Imagine a trunk with a lock that two people, Bob and Alice, use to ship documents back and forth. A typical lock has only two states: locked and unlocked. Anyone with a copy of the key can unlock the trunk if it's locked, and vice versa. When Bob locks the trunk and sends it to Alice, he knows that Alice can use her copy of the key to unlock the trunk. This is essentially how what's known as symmetric cryptography works: one secret key is used for both encrypting and decrypting, and both sides of a conversation use the same key.
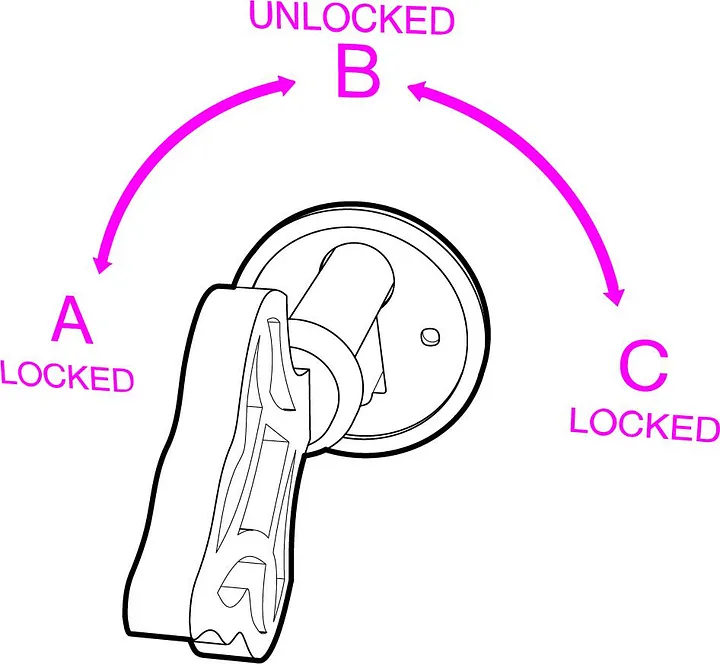
Now, imagine, instead, that Bob makes a trunk with a special kind of lock. This lock has three states instead of two:
A. Locked, key turned all the way to the left
B. Unlocked, in the middle.
C. Locked, key turned all the way to the right.
Instead of one key, two keys go with this lock:
Key No. 1 can only turn to the left
Key No. 2 can only turn to the right
This means that if the trunk is locked and the key is turned to position A, only key No. 2 can unlock it by turning right, to position B (unlocked). If the trunk is locked in position C, only key No. 1 can unlock it by turning the lock left, to position B.
In other words, either key can lock the trunk – but once it is locked, only the other key can unlock it.
Now let's say Bob makes a few dozen copies of key No. 2, the key that only turns right, and shares them with everyone he knows and anyone who wants a copy, making it his public key. He keeps key No. 1 for himself – it's his private key. What does this accomplish?
Alice can send Bob confidential data via the trunk and be confident that only Bob can unlock it. Once Alice has locked the trunk with the public key, which turns from left to right, only a key that can turn right to left can unlock it. That means only Bob's private key can unlock it.
Alice can be sure that the trunk is actually from Bob, and not an impersonator, if it's locked with his private key. There's only one key that can lock the trunk so that the lock is in position A, or turned all the way to the left: Bob's private key. True, anyone can unlock it with the public key by turning the key to the right, but it's guaranteed that the trunk is from Bob.
Substitute plaintext data for the trunk and cryptographic keys for the physical keys from this analogy, and this is how public key cryptography works. Only the owner of the private key can encrypt data so that the public key decrypts it; meanwhile, anyone can encrypt data with the public key, but only the owner of the private key can decrypt it.
Therefore, anyone can send data securely to the private key owner. Also, anyone can verify that data they receive from the owner of the private key is actually from that source, and not from an impersonator
In Cardano, there are two main key types:
- Address keys
- Node keys
Address Keys
Every user of Cardano can have two sets of keys and addresses:
- Payment Keys and addresses: To send and receive transactions
- Stake Keys and addresses: To control protocol participation, create a stake pool, delegate and receive rewards
Each set of keys has a private and a public key. They are sometimes referred to as .skey and .vkey
Payment Keys
To generate the Payment keys so that we can then receive and make payments we run:
cardano-cli address key-gen \
--verification-key-file payment.vkey \
--signing-key-file payment.skeyThis creates two files payment.vkey (the public verification key) and payment.skey (the private signing key).
Generate the hash of a payment verification key. This is a hash of a public key
cardano-cli address key-hash \
--payment-verification-key-file payment.vkey \
--out-file payment.pkhStake Keys
Then we need to generate a pair of stake keys. These keys are needed when delegating ADA to a stake pool
cardano-cli stake-address key-gen \
--verification-key-file stake.vkey \
--signing-key-file stake.skeyBoth verification keys (payment.vkey and stake.vkey) are used to build the address and the resulting payment address is associated with these keys.
Payment Address
cardano-cli address build \
--payment-verification-key-file payment.vkey \
--stake-verification-key-file stake.vkey \
--out-file payment.addr \
--testnet-magic 2With the address created you can now receive payments into. The address should look something like this: addr_test1qpkpxq5vn8uvwdkfels8vujft6x80w62lq6suwxck29m23azauccre8p54n33jswltx0wh56kukger4fjjvghtmy8ajquzhlr5
To query the balance of your account:
cardano-cli query utxo \
--address $(cat payment.addr) \
--testnet-magic 2Stake Address
To generate the stake address to participate in staking
cardano-cli stake-address build \
--stake-verification-key-file stake.vkey \
--out-file stake.addr \
--testnet-magic 2Test ADA
To get some test ada into your wallet go to the Cardano Faucet and request tADA into the address that you created in the previous step
In a few seconds, you should receive 1 000 tADA at you address. Query the UTXO to check that you have received it
cardano-cli query utxo \
--address $(cat payment.addr) \
--testnet-magic 2References
How does public key encryption encryption work
Explaining public-key cryptography to non-geeks
License
This work is distributed under a Creative Commons Attribution 4.0 International (CC BY 4.0) The license allows you to copy and redistribute the material in any medium or format, as well as remix, transform, and build upon the material for any purpose, including commercial, as long as you give appropriate credit to the creator.